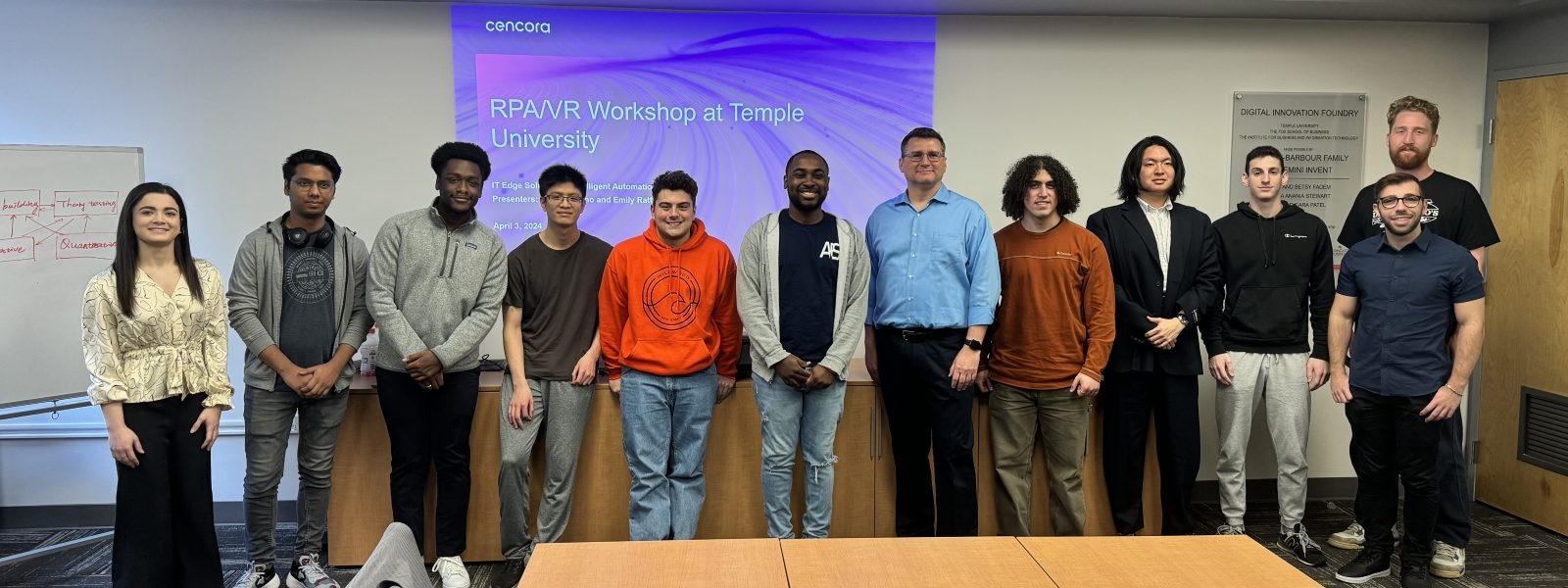
The Institute for Business and Information Technology (IBIT) engages with industry and its advisory board to develop knowledge and talent for the digital era.

Digital Innovation Foundry
The Digital Innovation Foundry (DIF) generates innovation by assessing, integrating, and prototyping digital technologies.

Advisory Board
IBIT works closely with senior industry leaders to develop knowledge and human capital across all of Temple University.

IS Job Index
Information Systems Job Index 2022
Scholarships
IBIT Corporate Scholarships recognize exceptional students.
Mitchel Zilbershteyn
Zhengkun Ye
Rachel Koffel
Abdalaziz Sawwan
David Levit
Ethan Chheda
Aashmun Doshi
Russell Abernethy